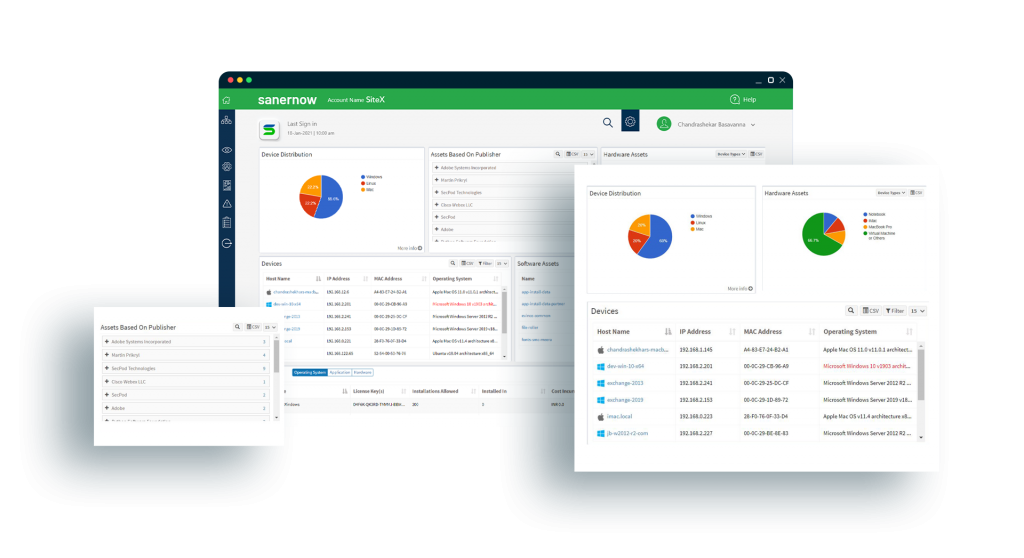
Get Holistic Visibility and Robust Control Over your IT Infrastructure
Gain Comprehensive Visibility and Control into your IT Infrastructure
Get All-Round Visibility and Control of Your IT Infrastructure
With SanerNow’s continuous and on-demand scans, you get live device and asset visibility and deviation detection to ensure nothing goes undetected. All from a single console!
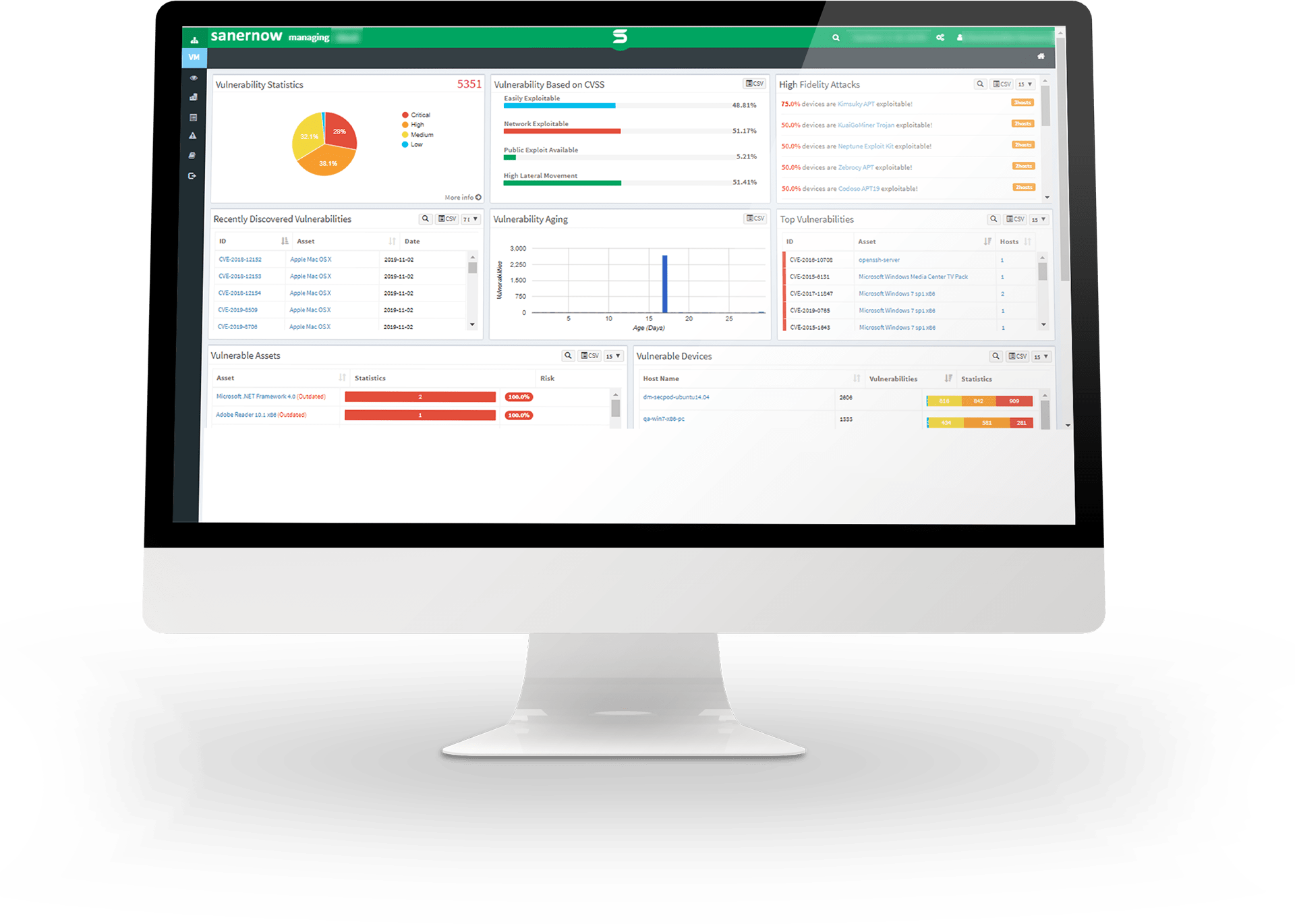
Accelerate Cyber Defense with Insightful and Intelligent Insights
Scan for devious deviations and receive insightful information about your organization’s security posture and take a never-seen-before look at your organization’s security posture
Implement IT Security Measures with Confidence by Eliminating Uncertainties
With SanerNow’s collective visibility, detect outliers, eliminate deviations and confidently implement your IT security controls
Leverage Machine Learning, Statistical Analysis, and Deviation Computation Methods to Control Anomaly Loopholes
Mitigate dangerous anomalies with SanerNow’s cutting-edge machine learning, statistical analysis, and deviation computation methods.
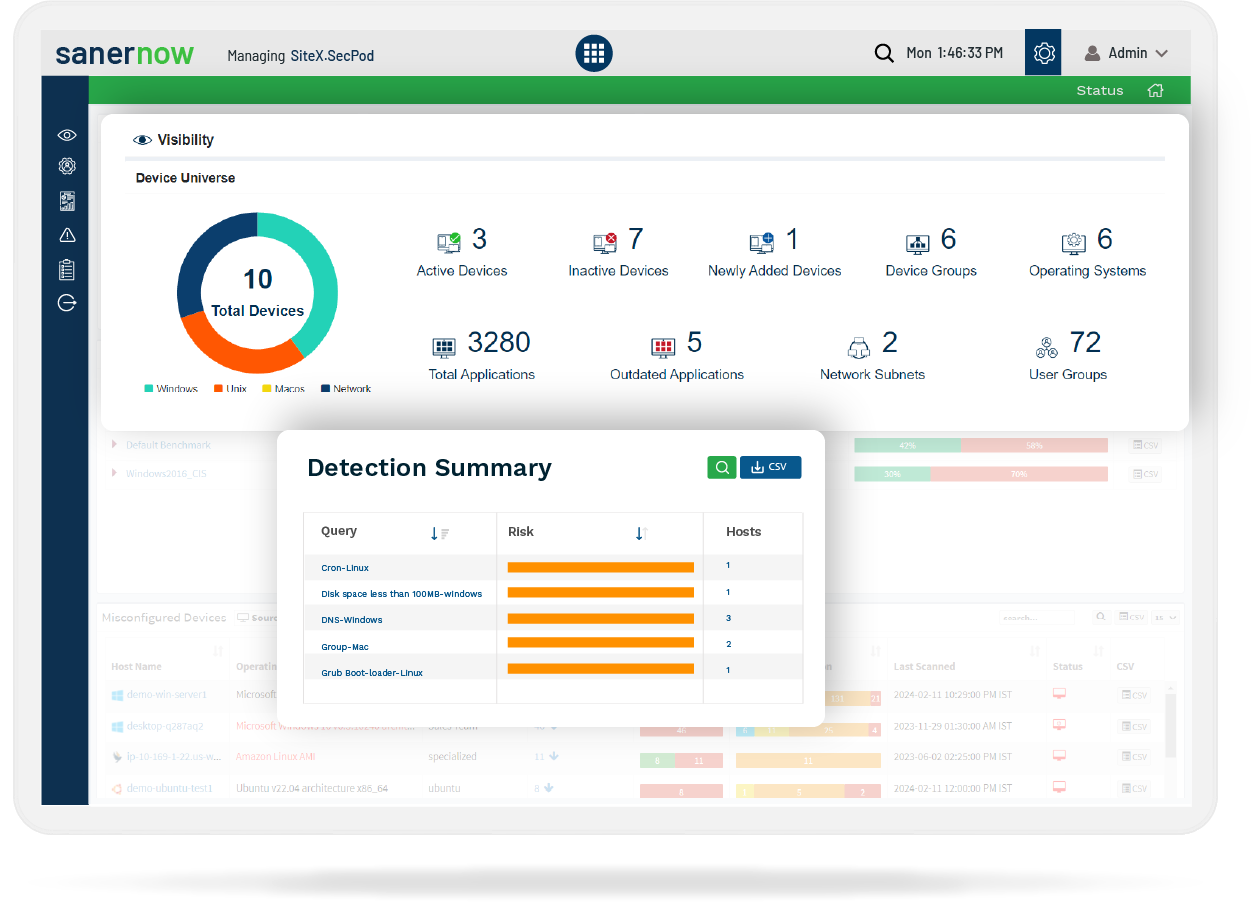
Achieve Seamless Visibility and Control Over Your IT Environment
Optimize Hardware and Software Visibility and Management
Track and monitor real-time usage of hardware and software assets in your inventory. Efficiently optimize your IT spend by removing rarely used and outdated applications through insightful reports.
Blacklist/Whitelist Applications and Manage Licenses from One Console
With an unified and aggregated dashboard, monitor IT asset in real-time, detect vulnerable applications, manage software licenses, and blacklist or whitelist them accordingly.
Intelligently Discover Anomalies and Receive Microscopic Look into IT
Discover dangerous anomalies through continuous scans 75+ anomaly computation rules. Monitor 2000+ device parameters to fetch insightful info into your IT network.
Anomalous Posture Detection through Statistical Anomaly Computation
Detect devious anomaly configurations like unusual command execution, atypical firewall configuration, and much more by performing collective statistical anomaly computation.
Known-Good your IT By Eliminating the Unrequired
With complete and holistic visibility, choose and whitelist the required devices and configurations alone. Remove the network anomalies and cleanse your IT.
Detect Deviations and Assess your Organization's Security Controls
From disabled firewall, poorly configured WiFi security, enabled autologon, outdates OSs and software, to disabled BitLocker, assess an array of security controls and spot the deviation in the settings that will harm the security posture.
Instantly Mitigate Detected Anomalies With Built-in Actions
With a slew of built-in actions, instantly remediate detected anomalies and deviations. Take a step further by creating custom detection and remediation rules, in single console.
Insightful Dashboard and Reporting to Evaluate your Security Posture
Generate intuitive reports that provide intelligent insights through creative visualizations. Always be audit-ready and utilize 100s of report APIs to create custom visibility .
Gain a Holistic View and Control Over Your Devices
Get free unlimited access and try it yourself.